[ad_1]
The infamous Lazarus Group of North Korean state-sponsored menace actors is at present focusing on susceptible Home windows Web Info Companies (IIS) internet servers to acquire first entry to enterprise networks.
Lazarus’ main motivation is monetary, and lots of observers suppose that the hackers’ nefarious deeds assist finance North Korea’s weapons-development initiatives. Nonetheless, the gang has additionally taken half in numerous covert missions. South Korean researchers at AhnLab Safety Emergency Response Middle (ASEC) are those who found the menace group’s newest tactic.
What We Know About Assaults on IIS Servers
Organizations of all sizes make the most of Home windows Web Info Companies (IIS) internet servers to host internet content material like web sites, functions, and companies like Microsoft Alternate’s Outlook on the Internet.
It’s a versatile answer that has been accessible for the reason that launch of Home windows NT, supporting the HTTP, HTTPS, FTP, FTPS, SMTP, and NNTP protocols. Nonetheless, if the servers are outdated or poorly managed, they’ll act as entry factors for menace actors.
In an effort to create information on the IIS server through the w3wp.exe course of, Lazarus first acquires entry to IIS servers using well-known flaws or configuration errors.
The menace actors drop ‘Wordconv.exe’, a legitimate Microsoft Workplace file, along with a malicious DLL known as ‘msvcr100.dll’ and an encoded file known as ‘msvcr100.dat’. The malicious code within the DLL masses when “Wordconv.exe” is launched in an effort to decrypt the Salsa20-encoded executable from msvcr100.dat and run it in reminiscence, the place antivirus packages can’t detect it.
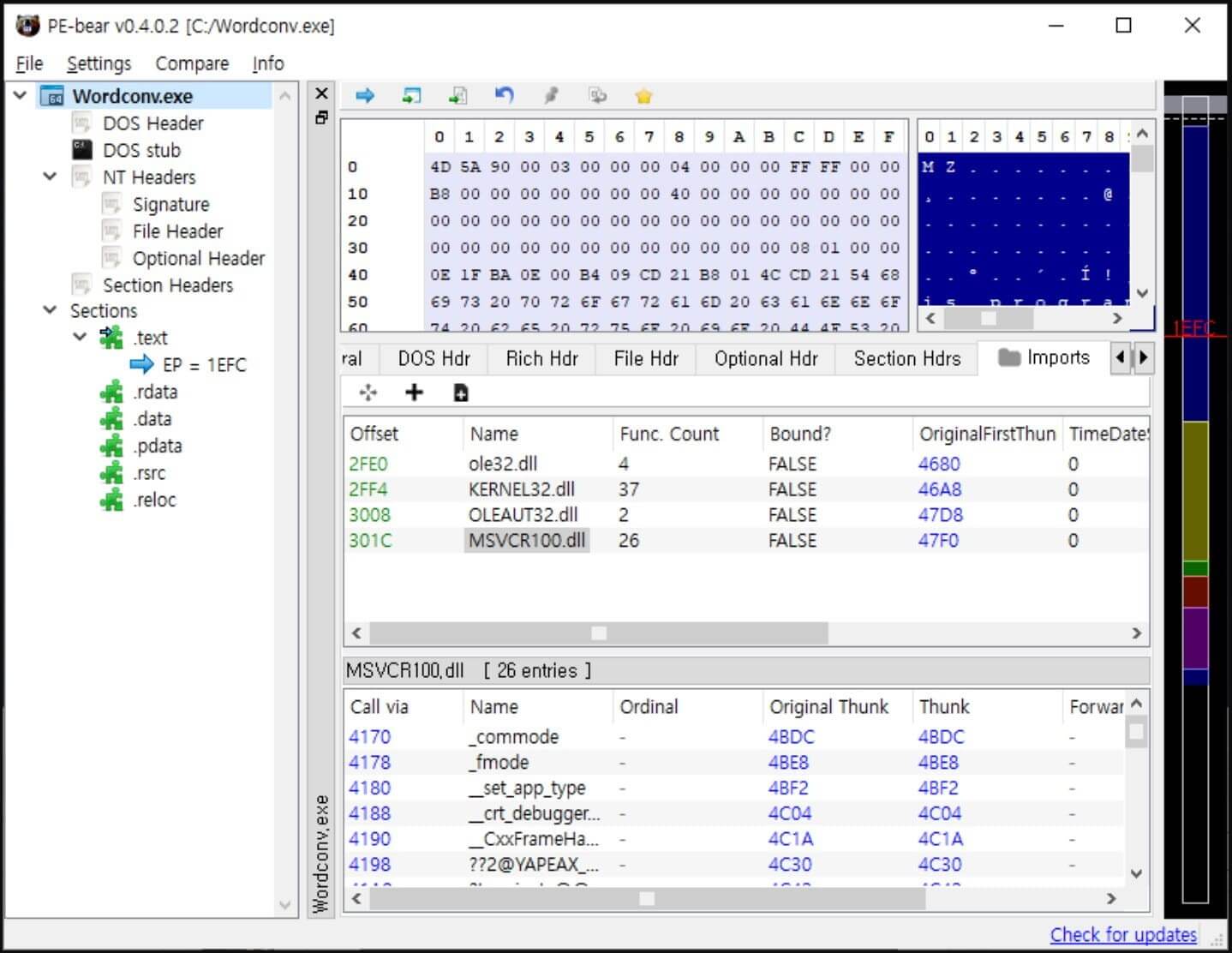
Import DLL Record on ‘Wordconv.exe’ (Supply)
The virus generally known as “msvcr100.dll” and “cylvc.dll,” which was utilized by Lazarus to deactivate anti-malware merchandise through the “deliver your individual susceptible driver” technique, share numerous coding similarities, in accordance with ASEC. Thus, ASEC considers that the newly found file is a brand new variant of the identical malware.
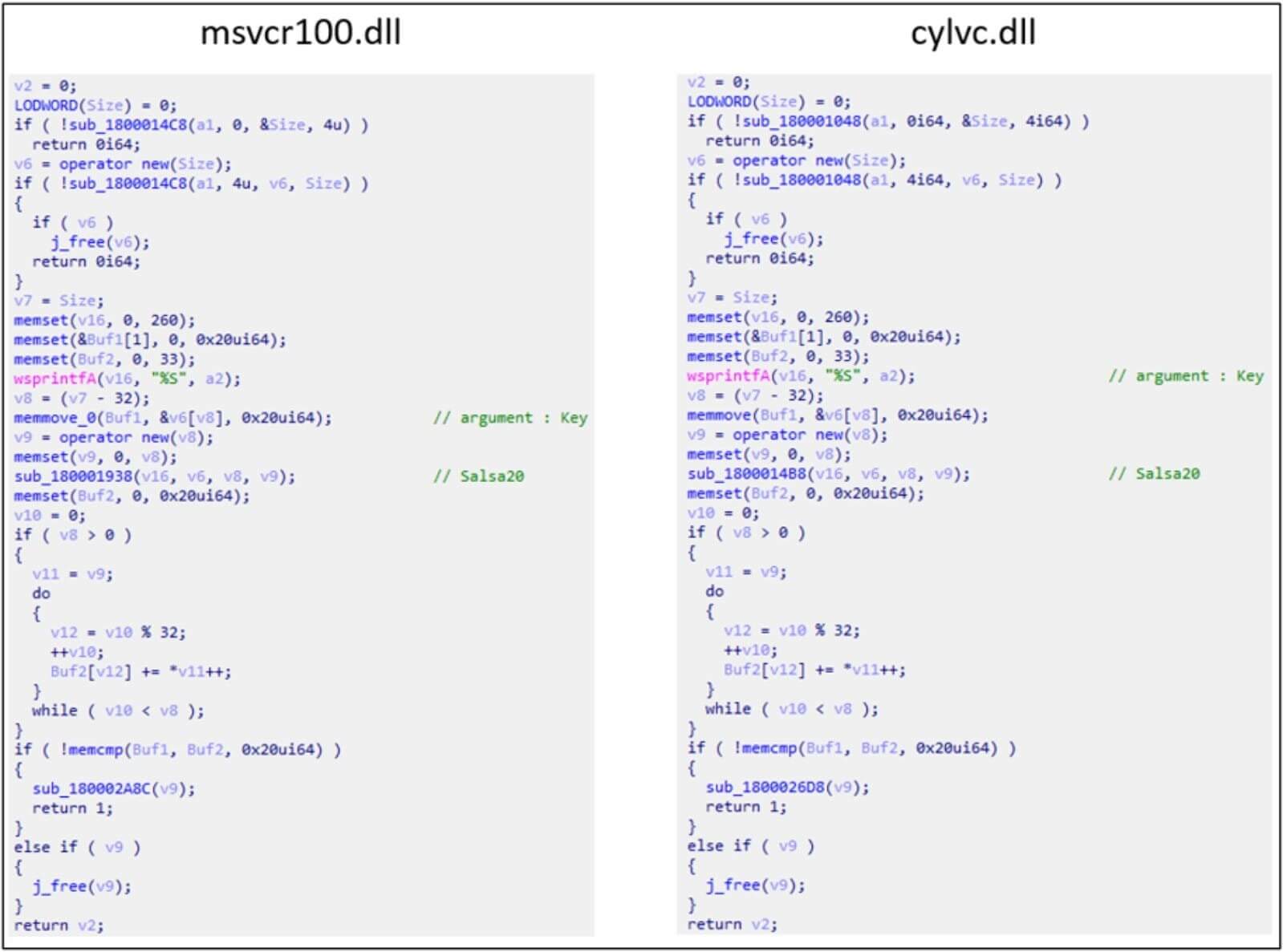
Lazarus proceeds the assaults by making a second malware (‘diagn.dll’) by way of the exploitation of a Notepad++ plugin. The second malware then receives a recent payload, this time encoded with the RC6 method, decrypts it utilizing a hard-coded key, and runs the payload in reminiscence to hide its execution.
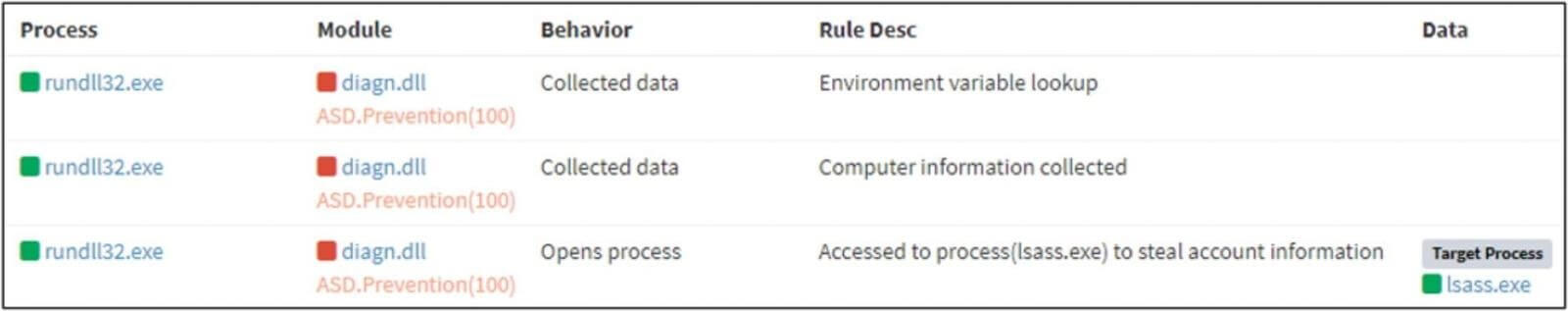
Utilizing reputable person credentials, almost definitely taken within the earlier stage, the Lazarus assault’s closing step was community reconnaissance and lateral motion by way of port 3389 (Distant Desktop). Nonetheless, in accordance with BleepingComputer, ASEC is but to uncover any additional malicious actions after the attackers unfold laterally on the community.
As a part of their assaults, Lazarus primarily depends on DLL sideloading, therefore companies are suggested to maintain an eye fixed out for uncommon course of execution.
In case you preferred this text, observe us on LinkedIn, Twitter, Fb, and Youtube, for extra cybersecurity information and subjects.
In case you preferred this put up, you’ll get pleasure from our publication.
Get cybersecurity updates you’ll really need to learn immediately in your inbox.
Unique Publish URL: https://heimdalsecurity.com/weblog/warning-lazarus-targets-windows-iis-web-servers-for-initial-access/
[ad_2]

