[ad_1]
A brand new phishing-as-a-service (PhaaS or PaaS) platform named Greatness has been leveraged by cybercriminals to focus on enterprise customers of the Microsoft 365 cloud service since a minimum of mid-2022, successfully reducing the bar to entry for phishing assaults.
“Greatness, for now, is simply targeted on Microsoft 365 phishing pages, offering its associates with an attachment and hyperlink builder that creates extremely convincing decoy and login pages,” Cisco Talos researcher Tiago Pereira stated.
“It comprises options similar to having the sufferer’s e-mail deal with pre-filled and displaying their acceptable firm emblem and background picture, extracted from the goal group’s actual Microsoft 365 login web page.”
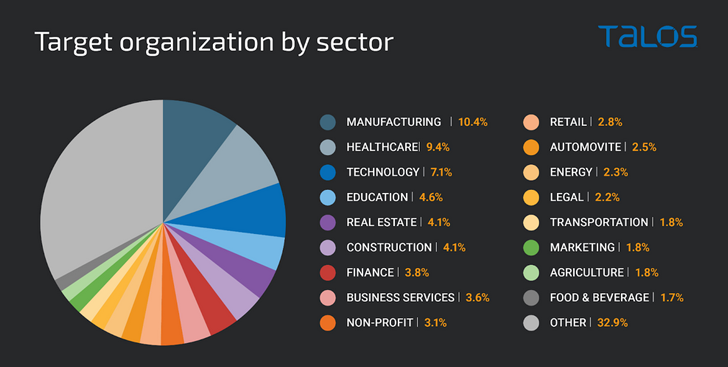
Campaigns involving Greatness have primarily manufacturing, well being care, and expertise entities positioned within the U.S., the U.Okay., Australia, South Africa, and Canada, with a spike in exercise detected in December 2022 and March 2023.
Phishing kits like Greatness supply menace actors, rookies or in any other case, a cost-effective and scalable one-stop store, making it potential to design convincing login pages related to numerous on-line providers and bypass two-factor authentication (2FA) protections.
Particularly, the authentic-looking decoy pages operate as a reverse proxy to reap credentials and time-based one-time passwords (TOTPs) entered by the victims.
Assault chains start with malicious emails containing an HTML attachment, which, upon opening, executes obfuscated JavaScript code that redirects the consumer to a touchdown web page with the recipient’s e-mail deal with already pre-filled and prompts for his or her password and MFA code.
The entered credentials and tokens are subsequently forwarded to the affiliate’s Telegram channel for acquiring unauthorized entry to the accounts in query.
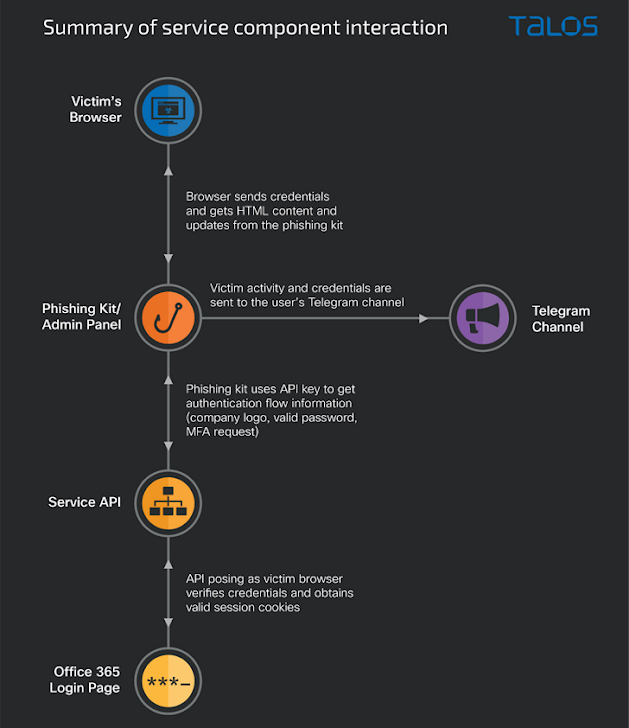
The AiTM phishing package additionally comes with an administration panel that permits the affiliate to configure the Telegram bot, hold observe of stolen data, and even construct booby-trapped attachments or hyperlinks.
What’s extra, every affiliate is predicted to have a legitimate API key so as to have the ability to load the phishing web page. The API key additionally prevents undesirable IP addresses from viewing the phishing web page and facilitates behind-the-scenes communication with the precise Microsoft 365 login web page by posing because the sufferer.
“Working collectively, the phishing package and the API carry out a ‘man-in-the-middle’ assault, requesting data from the sufferer that the API will then undergo the authentic login web page in actual time,” Pereira stated.
“This enables the PaaS affiliate to steal usernames and passwords, together with the authenticated session cookies if the sufferer makes use of MFA.”
The findings come as Microsoft has begun imposing quantity matching in Microsoft Authenticator push notifications as of Could 8, 2023, to enhance 2FA protections and fend off immediate bombing assaults.
[ad_2]