[ad_1]
Two “harmful” safety vulnerabilities have been disclosed in Microsoft Azure Bastion and Azure Container Registry that would have been exploited to hold out cross-site scripting (XSS) assaults.
“The vulnerabilities allowed unauthorized entry to the sufferer’s session inside the compromised Azure service iframe, which may result in extreme penalties, together with unauthorized information entry, unauthorized modifications, and disruption of the Azure companies iframes,” Orca safety researcher Lidor Ben Shitrit stated in a report shared with The Hacker Information.
XSS assaults happen when risk actors inject arbitrary code into an in any other case trusted web site, which then will get executed each time when unsuspecting customers go to the location.
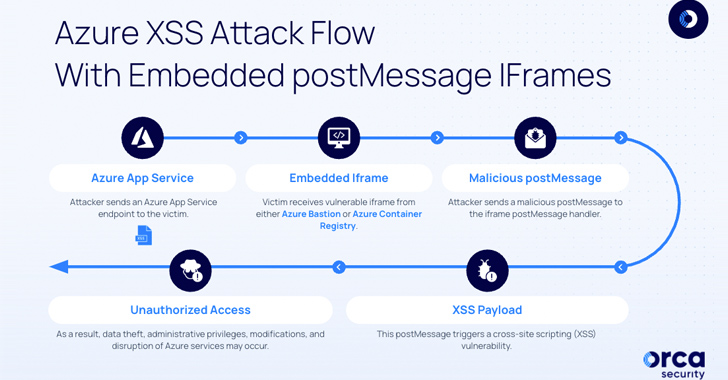
The 2 flaws recognized by Orca leverage a weak point within the postMessage iframe, which allows cross-origin communication between Window objects.
This meant that the shortcoming may very well be abused to embed endpoints inside distant servers utilizing the iframe tag and finally execute malicious JavaScript code, resulting in the compromise of delicate information.
Nonetheless, as a way to exploit these weaknesses, a risk actor must conduct reconnaissance on completely different Azure companies to single out weak endpoints embedded inside the Azure portal that will have lacking X-Body-Choices headers or weak Content material Safety Insurance policies (CSPs).
“As soon as the attacker efficiently embeds the iframe in a distant server, they proceed to use the misconfigured endpoint,” Ben Shitrit defined. “They deal with the postMessage handler, which handles distant occasions similar to postMessages.”
By analyzing the official postMessages despatched to the iframe from portal.azure[.]com, the adversary may subsequently craft applicable payloads by embedding the weak iframe in an actor-controlled server (e.g., ngrok) and making a postMessage handler that delivers the malicious payload.
Thus when a sufferer is lured into visiting the compromised endpoint, the “malicious postMessage payload is delivered to the embedded iframe, triggering the XSS vulnerability and executing the attacker’s code inside the sufferer’s context.”
? Mastering API Safety: Understanding Your True Assault Floor
Uncover the untapped vulnerabilities in your API ecosystem and take proactive steps in direction of ironclad safety. Be part of our insightful webinar!
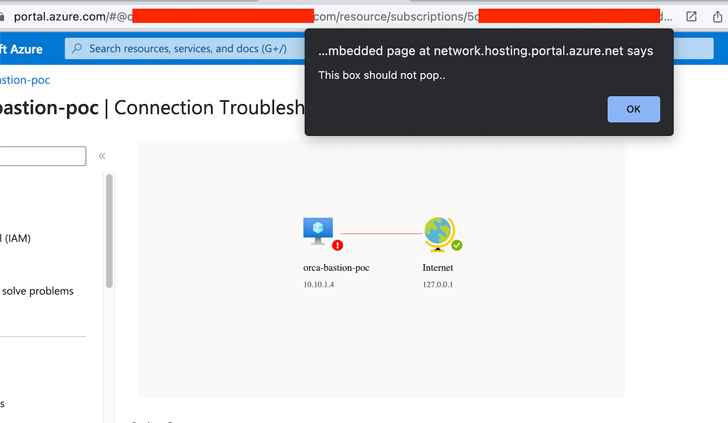
In a proof-of-concept (PoC) demonstrated by Orca, a specifically crafted postMessage was discovered to have the ability to manipulate the Azure Bastion Topology View SVG exporter or Azure Container Registry Fast Begin to execute an XSS payload.
Following accountable disclosure of the failings on April 13 and Could 3, 2023, Microsoft rolled out safety fixes to remediate them. No additional motion is required on the a part of Azure customers.
The disclosure comes greater than a month after Microsoft plugged three vulnerabilities within the Azure API Administration service that may very well be abused by malicious actors to realize entry to delicate info or backend companies.
[ad_2]